How to Set Up a Multi-Signature Wallet

A multi-signature wallet (or "multisig") requires multiple approvals before any transaction is processed. This extra layer of protection reduces risks like stolen keys or unauthorized access. Here's a quick breakdown:
Steps to Set Up:
Key Tips:
Multi-signature wallets are a smart way to secure your crypto, whether you're an individual or managing assets for a group. Follow these steps to protect your funds effectively.
Bitcoin 2-of-4 Multisig Wallet Tutorial using Sparrow Wallet in Testnet
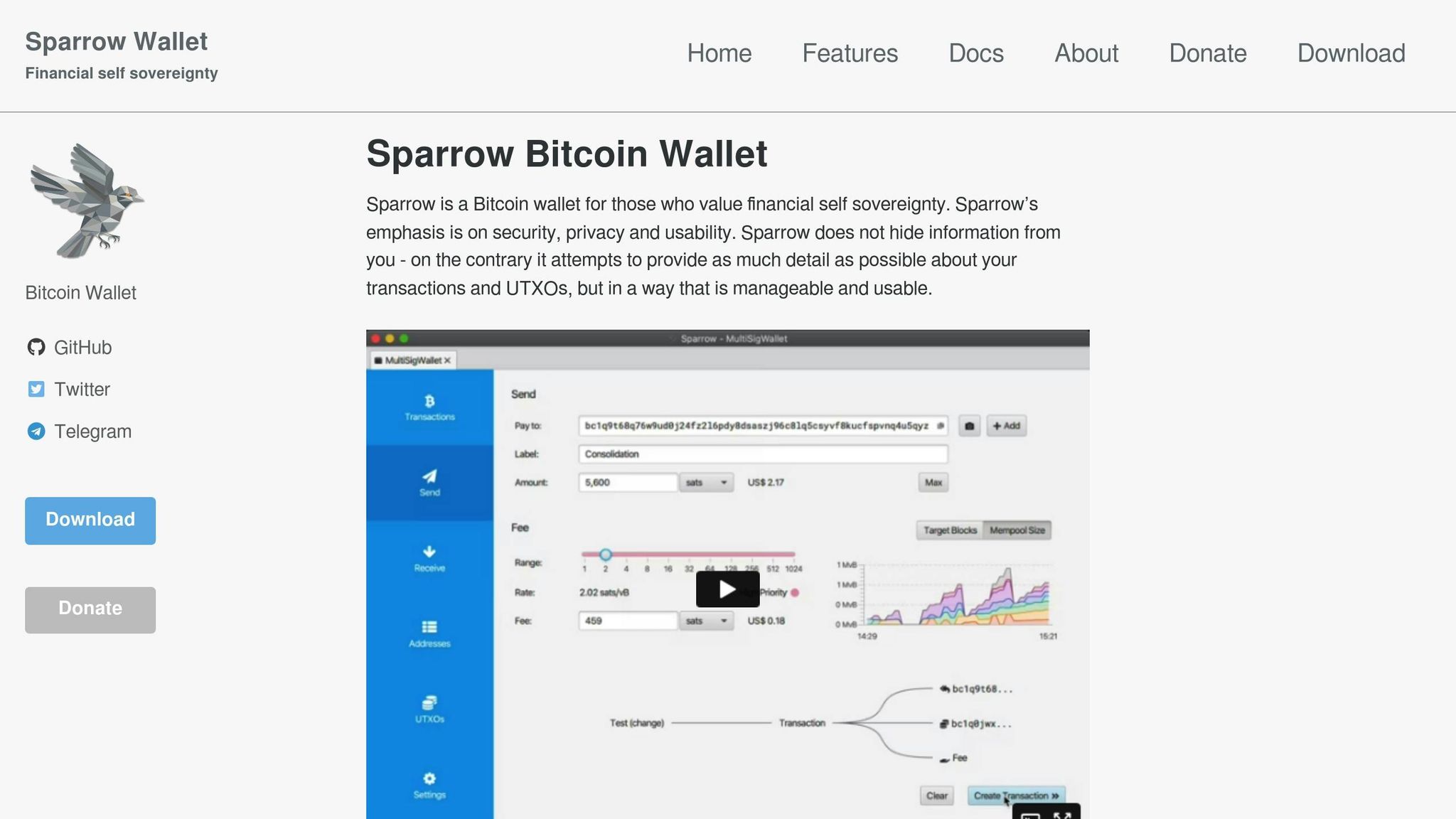
Choosing the Right Multi-Signature Wallet Platform
The security of your multi-signature wallet largely depends on the platform you choose. A reliable platform ensures smooth transaction management and robust protection for your assets. Considering that over 60% of cryptocurrency losses between 2021 and 2024 were due to hacks, selecting a platform with strong security measures is not just important - it’s essential. The right choice will balance ease of use with the enhanced protection multi-signature setups are known for. Let’s dive into some of the top platforms and the key factors to keep in mind when making your decision.
Top Platforms for Multi-Signature Wallets
There’s no shortage of platforms offering multi-signature functionality, but their features can vary significantly. Electrum is a favorite among advanced users, offering flexibility and detailed control over wallet configurations. If you’re looking for something more user-friendly, Casa and Unchained Capital are excellent choices. For both individual and institutional users, Coinbase delivers high-grade security tailored to diverse needs.
Some platforms are designed specifically for Bitcoin, while others support multiple blockchains. Your decision should align with the cryptocurrencies you plan to store and manage.
Key Criteria for Platform Selection
When evaluating multi-signature wallet platforms, consider the following:
By carefully weighing these factors, you can identify a platform that aligns with your needs while ensuring the highest level of security for your assets.
Why Hardware Wallets Are Important
Integrating hardware wallets into your multi-signature setup adds a critical layer of offline protection. These devices store your private keys offline, safeguarding them from online threats like malware, phishing, or hacking attempts.
Devices like Trezor and Ledger are popular choices and integrate smoothly with many multi-signature platforms. By spreading your keys across multiple hardware wallets, you reduce the risk of losing access to your funds. Even if one device is compromised or lost, your assets remain safe as long as the required number of signatures is maintained.
For businesses and organizations managing significant cryptocurrency holdings, this combination of hardware wallets and multi-signature setups is often considered the gold standard in security. When choosing a platform, ensure it supports your preferred hardware wallet models and test compatibility early to avoid potential issues later.
The small cost of hardware wallets is a worthwhile investment, especially for those managing large crypto portfolios. This extra layer of protection can make all the difference in keeping your assets secure.
Step-by-Step Guide to Setting Up a Multi-Signature Wallet
Here’s how you can set up a multi-signature wallet to enhance security and streamline approvals. Start by configuring your wallet settings, beginning with the right M-of-N setup.
Step 1: Decide on M-of-N Configuration
The first step is choosing how many total signers (N) you’ll have and how many signatures (M) will be required to approve transactions. In an M-of-N setup, M is the number of signatures needed, while N is the total number of keys or participants involved.
M-of-N Configuration
Security Level
Manageability
Use Cases
2-of-3
Medium
High
Small businesses, shared accounts
3-of-5
High
Medium
Larger institutions, DeFi projects
N-of-N
Highest
Low
Highly sensitive operations
For most users, a 2-of-3 setup hits the sweet spot between ease of use and security. It’s straightforward to manage three keys, and needing two signatures ensures solid protection without unnecessary complexity. If you’re looking for greater security and can handle more moving parts, a 3-of-5 configuration is a great option.
"The 3-of-5 setup is generally considered the sweet spot for balancing security and manageability. It provides high security by requiring a majority of keys while offering redundancy to handle key loss. For a simpler but still secure option, the 2-of-3 setup is also highly effective." - AirGap
Your choice should reflect how often transactions occur and how many people need to approve them.
Step 2: Generate and Back Up Keys
Key generation and backup are the most crucial parts of this process. Each key should be created on a separate device and stored in different, secure locations.
Here’s how to do it:
Before moving forward, test each backup by restoring the wallet on a separate device. This ensures everything works as expected.
Step 3: Share Public Keys
After generating your keys, share only the public keys (XPUBs) with the other participants. These keys are safe to share - they cannot be used to access funds but are necessary for setting up the multi-signature wallet.
To keep everything organized, create a secure document listing all XPUBs and the signer associated with each key. While public keys are less sensitive than private ones, store this document securely to avoid unauthorized access.
Step 4: Create the Multi-Signature Wallet
With all public keys collected, set up your multi-signature wallet on your preferred platform. The process may vary slightly depending on the platform, but the core steps remain consistent:
Once the setup is complete, confirm that the wallet address matches across all devices and participants. If the addresses don’t align, double-check the configuration before proceeding. Save the wallet configuration file, as it contains the public keys and settings needed to recreate the wallet later.
Step 5: Test the Wallet
Before transferring significant funds, test your new multi-signature wallet with a small amount. This ensures everything functions as expected and that all signers can approve transactions.
Each required signer must add their signature before the transaction can be broadcast. Depending on the platform, this may involve exchanging files or using built-in coordination tools.
Once funds have been successfully sent in and out of the wallet, your setup is ready for larger transactions. Document any issues that arise during testing and establish clear procedures for future use.
sbb-itb-d7b5bca
Best Practices for Security and Maintenance
Setting up a multi-signature wallet is just the beginning. To keep it secure and running smoothly, you’ll need to commit to regular maintenance and review. This ensures that your wallet stays protected and functions efficiently over time.
Implementing Advanced Security Measures
Advanced security goes a step further than the initial setup. For example, you can introduce time-locked transactions for large transfers, which add a delay before funds can be moved, requiring additional confirmations. Setting up notification systems is another smart move - these can alert all signers when a transaction is initiated or if any unusual activity is detected.
Regular security audits are a must. These should include penetration testing to identify vulnerabilities and reviewing access logs for suspicious patterns. Even minor security incidents should be documented to help you spot and address potential weak points before they escalate into bigger problems.
Periodic Key and Wallet Reviews
Once your wallet is set up, periodic reviews are essential for maintaining long-term security. Experts recommend a structured approach to wallet maintenance, as shown below:
Frequency
Action
Monthly
Verify all signatures are functioning
Monthly
Test recovery procedures
Monthly
Update firmware on hardware wallets
Monthly
Review access policies
Quarterly
Document all wallet configurations
Quarterly
Update emergency procedures
Quarterly
Confirm backup integrity
Quarterly
Review staking performance
Monthly reviews should focus on operational tasks, like ensuring all signers can access their keys and successfully complete test transactions. Firmware updates should be applied promptly to address any security vulnerabilities. Permissions should also be reviewed to ensure no unauthorized access has been granted.
Quarterly audits, on the other hand, provide a broader evaluation. These include documenting your wallet’s configuration, refreshing emergency plans to reflect changes in personnel or processes, and confirming that backups are intact and accessible. These deeper reviews help you stay ahead of potential risks.
Education for All Signers
Maintenance isn’t just about technology - education plays a critical role too. Everyone involved in your multi-signature wallet must be fully aware of their responsibilities.
"Educate all keyholders in signing transactions, secure key storage, and threat response."
It’s important to document procedures for tasks like signing transactions, performing firmware updates, and recovering backups. Regular training sessions can keep all participants informed about the latest best practices and potential threats. Clear guidelines should also address scenarios like key loss, signer unavailability, or changes in participation, with well-defined approval processes for these situations.
For instance, Gnosis Safe once successfully prevented a seven-figure fraud attempt at DAO Maker. This highlights the importance of having a clear and effective security policy.
Make sure your signature policy is written in plain language so it’s easy to understand during emergencies or when onboarding new participants. Including examples of transaction types and approval processes can be incredibly helpful during audits or when explaining your security approach. By prioritizing ongoing education, you can reinforce the procedures established during setup and testing, ensuring your wallet remains secure over time.
Troubleshooting and Recovering Multi-Signature Wallets
Multi-signature wallets provide an added layer of security, but they require careful setup and diligent key management to ensure smooth recovery if something goes wrong.
Common Setup Issues
One of the most important steps when setting up a multi-signature wallet is securely backing up all keys and seed phrases. Without these backups, recovering access to your wallet can become nearly impossible. If you’ve ensured proper backups, you can follow recovery procedures in case access is lost.
Wallet Recovery Steps
If you lose access to your wallet interface but have your backups intact, recovery is straightforward. Start by gathering all the backed-up public keys and seed phrases. Use these to restore the wallet based on your original M-of-N configuration. Remember, the M-of-N setup you initially selected dictates how many keys are needed to regain access. Most multi-signature platforms allow you to restore your wallet by re-entering the original public key order and configuration.
In 2018, Gerald Cotten, CEO of
, passed away unexpectedly. Since he was the sole person with access to the private keys securing the exchange's cold wallets, this tragic event resulted in $215 million worth of cryptocurrencies becoming inaccessible, affecting tens of thousands of customers.
If some private keys are lost but the number of remaining keys still meets the signature threshold, you can continue to access your funds. However, it’s best to set up a new wallet with fresh keys and transfer your assets to reduce future risks. Once you’ve regained access or if there’s a need to change participants, update your signer configuration as outlined below.
Adding or Removing Signers
Making changes to your multi-signature wallet setup, like adding or removing signers, must be handled with care to maintain security. To add a new signer, generate their public key and update the wallet configuration to include the new participant. If you’re removing a signer, ensure their authority is revoked in the active setup. Any changes should require multi-signature approval to ensure proper governance.
When modifying the signer list, consider how these changes impact your signature threshold. Adjust the configuration as needed to maintain both security and operational flexibility. Most multi-signature platforms support up to 20 signatures per transaction, giving you room to adapt as your needs evolve.
Conclusion
A multi-signature wallet stands out as a powerful tool for safeguarding digital assets. The numbers back this up: over 20% of all Bitcoin is permanently inaccessible due to lost keys or credentials, yet multisig solutions can cut the risk of internal theft by as much as 80% compared to single-user wallets.
This approach is also championed by leading voices in the industry. Ethereum co-founder Vitalik Buterin highlights the value of distributed security:
"An 'M-of-N' system ensures that funds are always accessible and recommends that keys be distributed among trusted individuals without revealing their identities to each other to maintain the security of digital assets."
The real-world success of this strategy is clear. Adoption is on the rise, with over 60% of major digital asset custodians now using threshold signatures and multisig wallets. Additionally, more than 30% of new DAO treasuries adopted threshold signature schemes in 2023, a significant jump from just 10% in 2021.
To integrate multisig wallets effectively, start with small-scale trials, document your signature policy, and maintain open communication among signers. Securely store backups, ideally using hardware wallets, to further enhance your protection. These steps are crucial for building a solid DeFi security framework.
For those eager to expand their knowledge of decentralized finance and advanced wallet management, platforms like Decentralized Masters (https://decen-masters.com) provide in-depth training. Their resources are designed to help you navigate DeFi complexities while implementing strong security measures for your digital assets.
With nearly 38% of institutional crypto thefts linked to poorly managed private key responsibilities, implementing multisig wallets isn’t just a precaution - it’s a necessity. Taking these steps ensures better asset protection and lasting peace of mind.
FAQs
What makes a multi-signature wallet more secure than a single-signature wallet for managing cryptocurrency?
A multi-signature wallet adds an extra layer of security by needing multiple private keys to approve a transaction. This means that even if one key is compromised, it alone isn’t enough to authorize any transactions, significantly lowering the chances of theft or unauthorized access.
These wallets also address the issue of single points of failure. By requiring multiple approvals, they’re better equipped to withstand cyberattacks or the accidental loss of a private key. On top of that, they’re an excellent solution for group management. With shared control and recovery options, multi-sig wallets offer a safer alternative to single-signature wallets, whether you’re an individual or part of an organization.
How can I securely back up and protect the private keys for my multi-signature wallet?
To safeguard your private keys and avoid potential loss, consider creating multiple encrypted backups. Store these backups in secure physical locations, like a fireproof safe or a safe deposit box, to protect them from physical damage or theft.
For added security, use hardware wallets or air-gapped devices for offline storage. These tools provide strong protection against digital threats, keeping your keys away from potential online vulnerabilities.
Make it a habit to regularly test your backups to ensure they function properly. Additionally, always verify wallet addresses on trusted devices to avoid errors. By following these steps, you can greatly minimize the risk of losing access to your multi-signature wallet.
What should I look for in a platform to set up a secure and user-friendly multi-signature wallet?
When selecting a platform for your multi-signature wallet, it's essential to weigh security and ease of use equally. On the security front, look for features like end-to-end encryption, support for cold storage, and robust authentication options to protect your digital assets. Choosing a platform with a strong history of security and positive reviews from other users can also provide extra reassurance.
For ease of use, prioritize platforms that offer a user-friendly interface and compatibility with multiple blockchains. Tools like customizable access controls and streamlined transaction approval workflows can simplify the process of managing your wallet. Striking the right balance between protection and convenience ensures your wallet remains both secure and practical to operate.
Related posts
- DeFi vs CeFi: Understanding Key Differences for Investors
- Exploring the Future of DeFi: Trends for Conservative Investors
- How Multi-Signature Wallets Secure DeFi Transactions
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"What makes a multi-signature wallet more secure than a single-signature wallet for managing cryptocurrency?","acceptedAnswer":{"@type":"Answer","text":"<p>A <strong>multi-signature wallet</strong> adds an extra layer of security by needing multiple private keys to approve a transaction. This means that even if one key is compromised, it alone isn’t enough to authorize any transactions, significantly lowering the chances of theft or unauthorized access.</p> <p>These wallets also address the issue of single points of failure. By requiring multiple approvals, they’re better equipped to withstand cyberattacks or the accidental loss of a private key. On top of that, they’re an excellent solution for group management. With shared control and recovery options, multi-sig wallets offer a safer alternative to single-signature wallets, whether you’re an individual or part of an organization.</p>"}},{"@type":"Question","name":"How can I securely back up and protect the private keys for my multi-signature wallet?","acceptedAnswer":{"@type":"Answer","text":"<p>To safeguard your private keys and avoid potential loss, consider creating multiple <strong>encrypted backups</strong>. Store these backups in secure physical locations, like a fireproof safe or a safe deposit box, to protect them from physical damage or theft.</p> <p>For added security, use <strong>hardware wallets</strong> or air-gapped devices for offline storage. These tools provide strong protection against digital threats, keeping your keys away from potential online vulnerabilities.</p> <p>Make it a habit to regularly test your backups to ensure they function properly. Additionally, always verify wallet addresses on trusted devices to avoid errors. By following these steps, you can greatly minimize the risk of losing access to your multi-signature wallet.</p>"}},{"@type":"Question","name":"What should I look for in a platform to set up a secure and user-friendly multi-signature wallet?","acceptedAnswer":{"@type":"Answer","text":"<p>When selecting a platform for your multi-signature wallet, it's essential to weigh <strong>security</strong> and <strong>ease of use</strong> equally. On the security front, look for features like end-to-end encryption, support for cold storage, and robust authentication options to protect your digital assets. Choosing a platform with a strong history of security and <a href=\"https://www.decen-masters.com/testimonials\">positive reviews</a> from other users can also provide extra reassurance.</p> <p>For ease of use, prioritize platforms that offer a <strong>user-friendly interface</strong> and compatibility with multiple blockchains. Tools like customizable access controls and streamlined transaction approval workflows can simplify the process of managing your wallet. Striking the right balance between protection and convenience ensures your wallet remains both secure and practical to operate.</p>"}}]}




